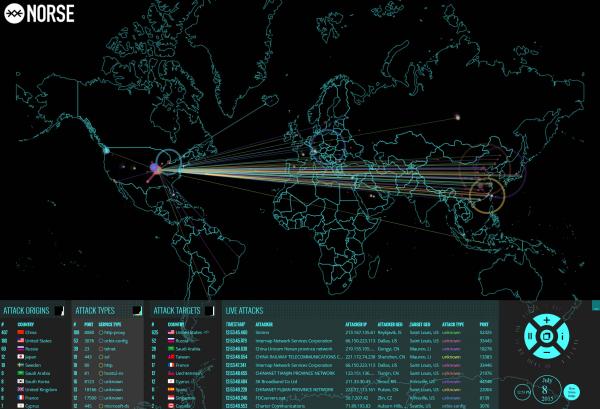
After a series of cyber failures involving first UAL, then this website, then the NYSE which is still halted, then the WSJ, some have suggested that this could be a concerted cyber attack (perhaps by retaliatory China unhappy its stocks are plunging) focusing on the US. So we decided to look at a real-time cyber attack map courtesy of Norsecorp which provides real time visibility into global cyber attacks.
What clearly stands out is that for some reason Chinese DDOS attacks/hackers seem to be focusing on St. Louis this morning.
(Read the rest of the story here…)